Attacks on the high-tech sector are targeting the infrastructure of broadcasters and OTT providers with a growing tendency. The same is also becoming increasingly common among providers from the areas of system- and software manufacturing, technology and service (cloud, mobile, telecommunication and cable operators). The consistent volume of attacks leads to the irrefutable conclusion that media & technology have established themselves as an attractive target for attacks.
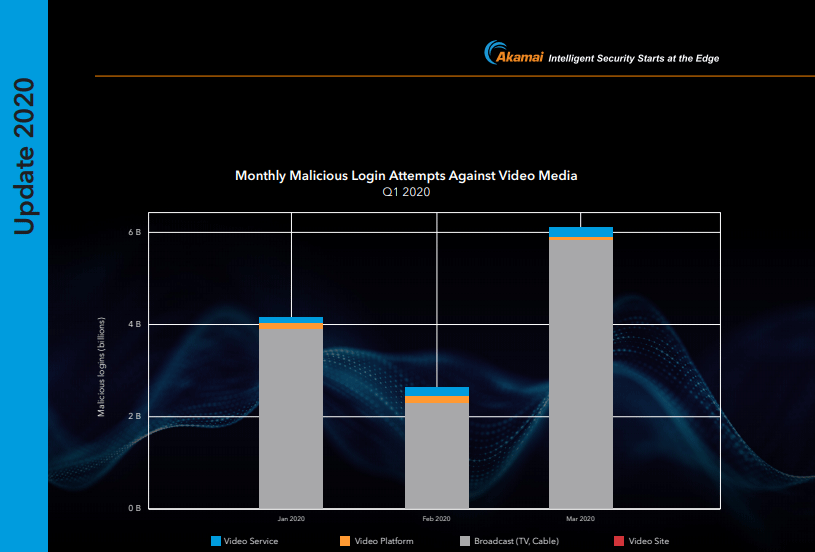
The current [state of the internet] / security report by Akamai deals, in particular, with attack techniques based on credential stuffing – essentially hacks with captured access data.
Info on this at Heise: “Credential Stuffing”: The Security Problem of Convenience – Attacks on user accounts often make use of the fact that users deploy the same access data for several services. However, this alone does not adequately describe the problem; the attack vectors of cyber attacks are much more diverse.
“black to air” – complete failure at broadcasters
„One of the biggest fears that broadcasters have is “black to air” — the moment when all the viewer sees is an empty screen. From a security point of view, Internet-based attacks such as Distributed Denial of Service (DDoS) are risks that broadcasters now have to think about across the supply chain. These are risks that have been around for decades in industries such as financial services. The new world of live IP TV, where much of the world’s media is consumed, means that any attack on availability could result in subscriber retention issues, hit ad revenue, and reduce the chances of future successful bids for rights.“ (Jaspal Jandu, Group CISO, DAZN)
Included in the current report:
- Overview of the topic
- Credential stuffing: developments 2018 / 2019
- Attacks on web applications: Sources and targets
- Methodology of attack vectors
- Summary
Download "Credential Stuffing in the Media Industry" - SOTI Volume 6, Special Edition Report
(PDF, English, 18 Pages)